With all the communication tools that businesses use today, there still is no more important option than the telephone system. Unfortunately for small businesses, the telephone system can be expensive and hard to manage. However, there is a way for you to get a fully featured telephone service with some of the most important tools your business needs, at a fraction of the price you currently pay for your enterprise telephone system.
k_Street Consulting, LLC Blog
Digital file storage has been a game-changer for many small businesses that rely on dynamic file retention. Instead of storing paper records in a huge room dedicated to file storage, businesses are focusing on digitizing their records and storing them electronically in cloud-based storage systems. This is a great alternative to all those printing costs.
When people talk about cybersecurity nowadays, there certainly seems to be a lot of emphasis put on phishing attacks and ransomware. This is for good reason. Not only can either of these attack vectors create significant difficulties for a business, they are often used in tandem. Let’s discuss why these threats are so potent, and why they so often show up together.
Working in IT for any length of time will make you understand that it isn’t just novice workers that have trouble with their computers. In truth, about seven out of ten people can’t diagnose and fix simple IT problems. With that truth, it’s evident that any business that relies on IT, or at least on the productivity of people who use workstations, needs to have some type of strategy to keep those endpoints up, running, and managed proficiently.
The technology your business uses is extremely important. One of the most important pieces of technology that you will routinely get is the workstation. Since it is the hub of productivity, there are certain variables that you need to consider when purchasing new workstations. This month, we will go through this process.
Many businesses need their employees to do the same thing day-in and day-out. With that type of repetitiveness, situations pop up where some crucial stuff is overlooked. Employees that are distracted with their own productivity are susceptible to making mistakes that could have dire consequences for your business. This month we thought we would give you a few pointers on how to communicate the importance of vigilance to your dedicated employees.
Every business owner wants to protect their data. Even if they don’t pour money into doing so, they typically still understand the importance of it. That’s why three-out-of-every-four businesses perform a backup at least once per week. It’s still good to be reminded how to make sure your backup can work for you. Let’s go over a few basic considerations to make if you want a data backup that you can trust.
Regulations are put in place for a reason: the data you keep is sensitive. Within certain environments, it is extremely important to know how to navigate so as not to mistakenly expose information that has no business being shared. This month, we thought it would be a good time to talk about how to navigate these highly-regulated environments to ensure success and security.
We all use computers to run our businesses every day, and data has become a key factor in what most businesses do. Even smaller businesses have begun to use their data for strategic purposes, and in doing so have started a trend that has taken the world by storm. Let’s take a look at the data services that are designed to inform business owners and decision makers on how their business is actually working and how to improve operational effectiveness.
You don’t need to be repeatedly told just how important risk management is. If you did, you probably wouldn’t have made it this far. One problem you see from business owners today is that while they understand just how many problems there are--and which ones they need to find solutions for first--they want to grow their company so fast that they overlook potential problems and end up hurting their business as a result. This month, we thought we would talk a little bit about contingency planning and how, if it is done right, it can have a marked effect on your business’ ability to carry-on after a problematic event.
In business, the more time your operations stutter, the more it costs. If downtime is extended, it can cause some serious problems for your business. This is true from the one-man band to the largest enterprise. This month we thought we would outline a couple ways that downtime can have a negative effect on your business aside from the obvious.
Cloud computing is a tremendous tool for modern businesses. It provides users with anytime-anywhere access to the applications, storage, and processing they need to keep business running efficiently and productively. It is billed as-a-service, meaning that it also comes with the flexibility and scalability most businesses need to control their computing costs. Unfortunately, it’s not always that cut and dry. Today, we are going to look at the hidden costs that businesses might see if they select to use cloud resources.
With businesses actively searching for ways to cut costs in the shadow of the COVID-19 pandemic, one place a lot of businesses are considering cutting is their printing initiatives. Today, there are several new solutions that can provide businesses options without having to rely on printed materials. If your business is one that cannot, however, you should know just how much your printer is costing your business. In today’s blog, we’ll review how you can calculate this investment.
Your business’ critical IT systems are on the fritz again, and you aren’t sure what’s causing the problem. Fortunately, you have access to help. When you don’t feel well, or something’s wrong with your body, you visit your healthcare provider. They’ll examine you, diagnose the problem, and prescribe a solution. This process has been in place for millennia. Much more recently, it was also adopted by a very different sector: the information technology industry in what is known as managed IT services.
With working from home becoming all but normal, a lot of workers are hoping that their foray into remote work isn’t going to come to an end anytime soon. Business owners who never would have considered letting their staff work from home are now finding that they are saving money and getting comparable (or more) productivity from their staff remotely. We thought we would just remind you that there are benefits to working in a dedicated office.
Would you know if the technology your business runs on hadn’t been updated for a while? How can you determine when your software licenses run out? Has your printer been serviced in the past six months? If you have no idea about the answers to these questions, you may be staring disaster in the face. Let’s discuss how you can answer “I don’t know” and not be in jeopardy of a catastrophic technology problem.
We’re halfway through the year, and I don’t think anyone expected 2020 to go the way it has. Many business owners are being extra cautious about their spending and doing what they can to prevent unexpected interruptions to their business. One costly interruption all businesses need to continue to prevent is data loss.
When a child asks their parents if they can get a dog (or a cat, a hamster, etc.) the typical reply from the parents is usually “you know, owning a pet is a LOT of responsibility…” It might be cliche, but it’s true, and there is a valuable lesson for a kid to learn when adopting a 4-legged friend. Computing technology might not be as cute, but it certainly comes with responsibility and plenty of lessons to learn.
Saving on capital expenditures is the successful business owner’s superpower. Today, a lot of the strategic cost cutting that is being done is through collaboration. When you increase the productivity of your staff, you can do more with less. Let’s look at some of the tools being used by successful organizations to enhance their productivity.
Security is unfortunately a major part of any business, and if there isn’t a diligent approach to the implementation of it, you can be left with huge holes in your network. Today, we thought we would discuss some of the best practices you can take to make sure that your organization’s security is in the best possible position to protect your digital resources.
If you are like millions of other non-essential workers, you’ve probably spent the better part of the past two months working from home. As a result, you may have considered repurposing an area of your living space to be a dedicated work area (assuming you didn’t have one already). If so, we have a few recommendations you should consider as you do so.
Running a business is often a circus. Many times, it requires several juggling acts and a dog and pony show to just get things done. This couldn’t be more true nowadays as business owners are considering how to get out from under the quarter where COVID-19 took away revenue streams and caused many businesses to temporarily close their doors. Today, we’re going to look at some ways you can stretch your capital to try and return to business-as-usual.
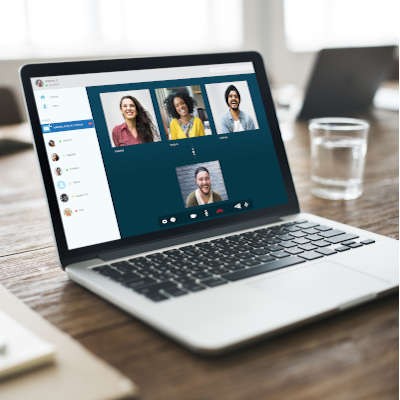
The COVID-19 pandemic has caused many people to begin working from home, necessitating remote communications to make sure that teams remain cohesive and business endeavors are fulfilled. One extremely useful tool for this purpose is video conferencing, as it is currently helping people keep some consistency in a very unsure time.
Despite how it might feel for many, the COVID-19 coronavirus outbreak is not the first time that humanity has dealt with such a serious health crisis. With the information technology we have at our disposal, we’ve been able to stifle the infection somewhat, with more innovation happening all the time. The same has happened at different times throughout history, so to keep our spirits up, we figured it would make sense to discuss how the darkest times also brought great progress.
“So, where have you been working?”
This isn’t an uncommon greeting when you haven’t seen someone in a while. With COVID-19’s influence, many people would answer that they have been working from home, if possible. While business owners may be resistant to the idea of remote work, the potential benefits make it possible that remote work is the silver lining to the coronavirus cloud hanging over us.
“It’s time to do some spring cleaning! It’s been put off long enough!”
It’s easy to let things pile up to deal with them at a later time, especially when you are on strict timelines and only have so many resources. That’s why my desk can look like a disorganized disaster some of the time (but in my defense, it cleans up very well when it needs to).
The average person’s mobile plan comes with a data cap. It’s for this reason the Wi-Fi hotspot is looked on as an essential tool, especially with so much content available nowadays. With 5G on the horizon, some reports have suggested that Wi-Fi will be phased out by ubiquitous wireless Internet access. Turns out, in the immediate future, the Wi-Fi hotspot isn’t going anywhere.
There are a lot of businesses that use cloud computing. In fact, the latest figures say that over 80 percent of businesses are now using some type of cloud platform for their operations. Of course, there are a lot of different options available to organizations, but one particularly useful solution that may not get a lot of attention is the unified communication platform. This month, we’ll take a look at the cloud-hosted communications platform.
Humans are social creatures, and as social creatures we create systems that separate us by our differences. IT professionals are known as such because they are experts at understanding and working with computers and information systems, just as Olympic gymnasts are regarded for their ability to compete in gymnastic events. Our differences are our identifiers. In fact, humans put labels on things to better identify them using even the most miniscule differences.
Contracts are a huge part of doing business. The practice is as old as the legal profession. You’ll be hard pressed to complete a transaction where money changes hands where there isn’t a document outlining the specifics of the liability each party takes on by entering that financial agreement. We call them receipts, but in retail, they are a signed contract.
The way your business accesses data is changing. Just a few years ago, you couldn’t imagine that you would have a comprehensive strategy to keep data secure when sending and receiving it wirelessly, but today wireless transmission methods have become more secure, reliable, and fast. Today, we’ll take a look at the difference between wired and wireless connections in the modern business.
Each and every business should be prioritizing their cybersecurity, as hacking is as popular and ever and some of the worst malware in history is currently spreading. To really drive this point home, we’ve put together some telling cybercrime statistics that clearly demonstrate the damage that cybercrime can wreak.
It may not seem like it, but the mobile device is very much like the Internet. They’ve both only been around a short time, demand for each is massive, and their mere presence has changed modern life. Today, we’ll take a look at how the mobile device came to be and give you a brief look at mobile device history.
The Internet has expanded people’s ability to do business, and with it has spurred on a series of innovations that have effectively changed the world. With today’s businesses almost assuredly spending on at least one cloud-based solution, and with mobility eking into almost every business in one form or another, the demand for more bandwidth is something most businesses are wrangling with. Today, we’ll describe what having enough bandwidth means.
Today, cloud services can be used for about every facet of business. In fact, your business probably uses the cloud for some very important parts of your business. With so many options to choose from, business owners often develop a cloud strategy that includes software as a service (SaaS), infrastructure as a service (IaaS), and many more options.
Much is made about collaboration. It’s not just a buzzword, it is extremely important in many parts of business. Collaboration is simply getting people to cooperate in their work to a successful end. While collaboration can be found in every business to some degree, it can be more of a challenge for the small business. Today, we’ll take a look at what constitutes successful collaboration, and how your organization can go about improving your collaborative capabilities.
When people talk about cybersecurity nowadays, there certainly seems to be a lot of emphasis put on phishing attacks and ransomware. This is for good reason. Not only can either of these attack vectors create significant difficulties for a business, they are often used in tandem. Let’s discuss why these threats are so potent, and why they so often show up together.
Cybersecurity needs to be one of any business’ primary considerations. More than it ever has been before, cybersecurity is one of the biggest day-to-day issues that a business needs to deal with; and, this need is only exacerbated by the shortage of cybersecurity talent and loyalty to outdated security strategies have put many businesses in an unenviable, and vulnerable, position.
January 14 marks the end of two Microsoft operating systems: Windows 7, and Windows Server 2008 R2. After these titles are retired, using them could quickly result in a major problem for your business’ IT security. If you haven’t made the switch to other solutions by now, you are running out of options. Let’s quickly go over what you can do.
Sometimes a virus or malware infection can be so bad that the best solution is to completely wipe the device and start over with a factory reset. This can be pretty annoying. A new type of malware targeting Android devices just found a way to become even more annoying by being able to withstand a complete factory reset.
There are times when people take their technology for granted. One of the most under-the-radar, yet crucial parts of a business’ technology infrastructure is the networking equipment. What we mean by this is the cables, switches, and routers that connect computers to the network and to the Internet. This month, we will take a look at typical office networking found in 2019 and the technologies that are primed to replace them.
To build anything great on a budget or a timeline, you need to have good coordination. At the helm of these projects is the project manager. A job that is extraordinarily stressful and often equally thankless. After all, most customers take the positive resolution to any order for granted. This month, we will take a look at project management and the tools that are used by them to produce the best results possible.
The cloud is the new standard for businesses to handle their data storage and software distribution needs. We have a lot of experience in assisting our clients with the services they use via the cloud, and beyond that, most people are somehow connected to “the cloud” in some shape or form. However, this does raise a few questions about how secure our data actually is.
When many businesses look to add to their roster, they typically have a series of qualifications they need each applicant to meet before they grant interviews. They make their selection, do their entrance training, and then expect that the new hire will settle in and be as productive as possible as soon as possible.
Data privacy is a huge issue right now, and with so many organizations possessing individual information, the issue isn’t going to be going away. Some of the biggest and most reputable organizations in business today have been breached in the past several years and it has put a new onus on individual data protection. Let's take a look at individual data privacy and what can be done to protect yourself online.
With technology trending up, it’s not hard to believe that there are solutions out there that can give your business a leg up on the competition. Being a decision maker at a small or medium-sized business, it can sometimes be difficult to find technology solutions created with your business in mind. Most software developers understand that the more options their software has, the more valuable it is, but if you are a small business, enterprise software can sometimes be overkill. Let’s look at three technology trends that have small businesses in mind from the get-go.
When you start looking at your company’s communications costs, you may not always like what you see. If you think you are paying far too much for far too little, you aren’t alone. Many businesses just like yours are making the switch to communications tools that can be leveraged through the Internet. This month, we will take a look at some of these solutions.
A lot of business owners kick the tires on mobility before moving onto committing capital to other facets of their IT. When we write about mobility typically what we mean is a commitment to technology that allows staff to work on company projects, access company resources, and do it all from remote locations. This month we’ll talk a little bit about what it means to enhance your operational and staff mobility and provide you some solutions that will facilitate that change for your company.
October is National Cybersecurity Awareness Month, and we thought we’d share some of our very best tips and tricks to help you and your business keep your data and network safe in the modern ever-changing threat landscape. Cyberattacks can happen anytime, so being aware is crucial. That’s why cybersecurity in the modern business starts with you. It is your job to keep information safe. Sure, you can improve the tools you use to keep your infrastructure free from threats, but ultimately, to protect this data, you will need to stay vigilant.
We are constantly advocating the usefulness of having a comprehensive data backup and disaster recovery system in place. This is because you never know when some detrimental situation is going to negatively affect your information systems, and being prepared for that eventuality is a prudent business decision. In the modern office, the need for BDR grows rapidly. Today, we’ll take a look at our BDR solution and how every office absolutely needs one.
Working in an office can often be a grind. People that have never experienced it may not realize just how much coordination is needed to perform successful service delivery and support. One way the modern office functions is with the help of integrated technology. This month we will take a look at the modern office, the technology used by the office staff, and how the managed IT service provider can help build operational efficiency.
Most businesses think about Microsoft Office when the topic of Microsoft comes up, or at least Microsoft Windows. One of the services that has flown somewhat under the radar is Microsoft Azure, the tech giant’s cloud computing platform. What are some of the biggest selling points for Microsoft’s proprietary cloud computing solution, and what does it mean for your business?
Chances are, during your time running a business, you’ve thought at least a little bit about how best to distribute Microsoft Office software to your employees. Of course, the answer is never the same, so we recommend taking a look at what some of the options are before making your choice. In particular, we think the decision between Microsoft Office 2019 and Microsoft Office 365 will be an important one to address.
Many businesses struggle with the reality of everyday IT issues, one of which is receiving the right kind of support and maintenance to ensure everything goes according to plan. When considering your business’ IT maintenance and management, you need to consider the service provider, the distance they travel to and from your office, and ease of support. How can you make sure that your business finds the right solution or service?
Twenty years ago, the term “Internet of Things” was coined by a marketer named Kevin Ashton. Working for multinational consumer goods corporation Proctor & Gamble, his idea to use RFID to help manage P&G’s supply chain led to a partnership with MIT. For his efforts, Ashton became a high-tech entrepreneur and best-selling author, but his lasting legacy will likely be tied to the actual Internet of Things (IoT).
Windows might be the most popular operating system out there, but it’s not perfect. This is why your systems receive patches and security updates as they are released. The problem, however, is that these updates don’t last forever, and one of the most popular Windows systems out there will lose access to support on January 14th, 2020. Are you going to update now, or are you going to risk your systems going without critical updates?
Telephones have been in the office for so long that it would be weird if they weren’t in the office in some way, shape or form. With the advent of cloud-based options, however, telephone communications have become much more sophisticated and accessible. A voice over IP system that uses the Internet is one way that you can take advantage of modern technology to reduce costs and optimize your network.
We talk a lot about managed services for small and medium-sized businesses, but unless you’re familiar with the business model, you won’t be able to learn much about who we are and what we provide to organizations like yours. Today we are hoping to clear up some definitions of managed service providers, or MSPs, as well as what kind of services we can provide for businesses with limited budgets.
In the business world, it’s natural that you encounter those that want to see you fail, but there are also those that simply want to piggyback off your success. In many ways, security threats are a little bit of both, as they can potentially steal your data and leverage it to their benefit, as well as cause harm to your organization. We’ll dig into some of the details of the most common security threats and the risks they cause for your business.
The Internet of Things is a phenomenon that must be accounted for, as the sheer number of devices accessing networks means that security is always a concern. How can your organization be sure that the Internet of Things doesn’t create problems? It all starts by being aware of how your organization’s network infrastructure operates in relation to the Internet of Things.
Downtime can be devastating for your business if you allow it to persist. Unfortunately, many businesses don’t have the mindset needed to keep downtime from influencing operations, and it’s most telling when a disaster strikes. We’re here to help you understand downtime, its effects, and what you can do to prevent it.
It’s hard to think about the modern office without considering the role that information technology plays in it. If you think about it, it wasn’t so long ago that organizations were struggling with gaining access to important resources and maintenance, but sometimes it’s important to reflect on the way things were before IT infested offices all over the world. Let’s discuss how the IT-less office functioned before and after technology solutions were implemented en masse.
Email is generally considered to be one of the more effective ways of communication in the business world. An organization that can use email adeptly is one that saves time and money. Today, we’ll be discussing how you can get the most out of your email solution through the use of best practices and other tips.
It doesn’t matter how intensively a business uses their technology, there will always be a need for maintenance of some sort, whether it’s something as simple as a point-of-sale system or a full-fledged desktop workstation. Some businesses might have a complete IT department, while others might not have the resources to allocate to this role. We’ll walk you through how, no matter what kind of organization you operate, your business can benefit from a help desk solution.
Cybercriminals have been altering and ramping up efforts to steal data for much of the past decade. Once thought to just be a nuisance, now it has become evident that the cost of doing business now includes comprehensive network security strategies, designed to keep threats from affecting your business’ ability to create revenue. Let’s take a look at a working cybersecurity strategy.
A data loss incident might seem like an abstract concept, but it’s really quite simple when you boil it down to one cold, hard fact: your business suffers from downtime and it can no longer function the way it’s supposed to. When facing down a data disaster, there are a lot of ugly truths that your organization needs to be prepared to address. Here are three of them.
It’s one thing to implement password security for your business, but another entirely to convince your users that it’s for the best in regards to network security, rather than implementing it as an annoyance to them. Your organization should make using new passwords and best practices as easy as possible to expedite the security process.
There are many threats out there in the online world that want to see your business suffer, and they will go to any lengths to make it happen. Now, we all have seen the various emails that these hackers and scammers might send to unsuspecting users, but these are only the beginning. The real threat comes from specialized phishing attempts, and they come in many different forms. We’ll help you identify them.
Does your organization take network security as seriously as it should? It’s easy to forget with today’s advanced security offerings that the online realm is a dangerous place, but the truth of the matter is that you can’t risk your business’ security--not even for a moment. We’ll walk you through how your organization can minimize threats to security, as well as give you a primer regarding what’s at stake.
Cybersecurity is one of those hot-button issues that you should understand well enough to protect your business and yourself. Basically, as your organization holds more sensitive information, you’ll need to be more vigilant about how you approach cybersecurity. Today, we’ll take a look at the design and practices of organizational cybersecurity, and how you can work to bridge the gap between the solutions you can’t afford and the ones you already use.
The modern business has a lot more to worry about than ever. Businesses that rely on a supply chain - especially those that have a distribution wing - have to be in a position to manage every facet of the process. At one time this process was done entirely by phone, but with software that provides the opportunity to manage multiple parts of a business now available, and with shipping companies now utilizing technology to handle their own operations, the modern manufacturer now has a solution to improve their effectiveness.
Just like plenty of other industries all over the world, the manufacturing industry is beginning to take advantage of new IT solutions. Manufacturers can benefit considerably from implementing new and improved technology, including solutions connecting the Internet of Things, Asset Management, and Big Data analytics to their current IT approach.
In a sense, your business relies on its vendors to provide the goods and services needed to make your organization function. Think about your Internet service provider. They provide you with a service that connects you to important assets. The software your business utilizes is also provided by vendors, and work probably can’t get done without it. Therefore, it’s natural that you will want a good relationship with vendors… provided they are actually decent vendors themselves.
Mobility is a key part of today’s modern workplace, as employees are using devices to take data on the go with them for anytime-anywhere productivity. Unfortunately, this flexibility and mobility comes at a price. Taking data outside the safety of your network is more risky than ever before, to both data being sent to and from the device. The use of a virtual private network, or VPN, can remedy this issue.
You never know when your organization might fall prey to a disaster, whether it’s something natural that you can’t predict or a user error from even the most vigilant employee. We’ll walk you through what some of the most common office disasters are and how you can make sure your organization survives them with ease.
Wouldn’t it be useful if you could keep multiple versions of files just in case you make a mistake on one, or it’s been lost, or it has been altered in a way that makes it hard to fathom what the person who worked on it last was thinking? File versioning can be extremely helpful for businesses, as without it, the possibility of a file that is being worked on constantly being lost or damaged is a considerable threat. Let’s take a look at what file versioning does for businesses and how you can take advantage of it.
It’s easy to fall into the trap of thinking about data backup as something unnecessary. After all, the only reason to ever have it is if you somehow experience a critical data loss situation, and that’s extremely unlikely… right? It’s the wrong mindset to have, especially if you want to think about your business’ future. Your data backup and disaster recovery solution can prevent this, but only if you can find a solution that keeps downtime low without compromising what data is protected.
Security continues to be a major pain point for businesses of all shapes and sizes, and with the overwhelming volume of new and emerging threats hitting the scene on a daily basis, many professionals have turned to automated solutions based around artificial intelligence to fight back. While this presents a considerable benefit, it also creates other issues that need to be addressed if we want to take advantage of it in the years to come. Is there a way to use A.I. for network security without putting your business at risk?
There are very few industries more reliant on compliance and proper procedures as the healthcare industry. Since healthcare depends so heavily on medical technology, the management of this IT becomes a focal point that must be considered when planning out any infrastructure or data dissemination policy. However, artificial intelligence could change this for the better. Here’s how.
At first glance, the Internet of Things is confusing, but now that we’ve been seeing “smart” devices hit the market for some time, there are understandably a few very serious issues that come with so many devices being able to be accessed from the Internet. The utilization of “smart” devices carries value. Here we have machines that do a lot of the heavy lifting for us in our lives, and with the ability to remotely control them, they only become that much more valuable.
There aren’t many technological assets as important for the modern business than its communications solutions. The telephone, while being one of the oldest currently-utilized communications systems available, is still the most utilized. Today, we will look at business telephone systems and why choosing Voice over Internet Protocol simply makes sense for your business.
Countless threats stand between your business and productivity, even if modern security solutions have prevented the majority of them from ever becoming a problem. The fact remains that, unless you’re being proactive about security, your organization could face a considerable challenge in keeping its network secure from intruders. We’ll delve into what some of these threats are, why they are such an issue, and what you can do about them.
Ah, the holidays; they are a time for good food and good cheer, but also tend to be a time of gift-giving of all kinds. You might have all kinds of new gadgets running around your office that aren’t being accounted for. Some of these devices might be a security issue for your business precisely because they aren’t normally meant to connect to the Internet. These Internet of Things devices just aren’t as secure as they should be, especially in a business environment.
Anyone that has spent any time online recently is sure to have come across something they’ve perceived as deplorable. For all the good that it does, some of the most divisive of human interaction happens on the web. Since it really depends on your perspective just how much negativity you take from the Internet, we’ll go through the good, the bad, and the ugly of the Internet to put into perspective just how it affects our lives.
Businesses need to be prepared for the worst these days, as disasters could strike at any moment and cause irreparable data loss. One of the ways your business can break in the new year with confidence is with a backup and disaster recovery strategy that minimizes downtime and keeps your organization safe from events beyond your control. We’ll help you put together the best backup solution for your business’ needs.
You’ve probably heard the term “blockchain” at least a couple of times over the past year, but what does it mean, and how are organizations using it? The most obvious and well-known use for it is cryptocurrency, but it’s far from the only use of blockchain. We’ll delve into what blockchain technology is, how it is currently used, and how it might be used in the future.
2017 wasn’t so long ago, but one year is a long time in terms of cybersecurity developments. Anytime the Internet is involved, it’s important to remember that threats have access to the collective minds of every hacker on the planet, meaning that developments can happen rapidly and without much warning. We’ll take a look at how cybersecurity has changed since 2017, including some notable information about how organizations are protecting themselves today.
If you’ve read any of our content, we continually stress the importance of innovation. Learning how to adjust and do things better allows for any organization to maximize productivity. In doing so, it creates the environment needed to become a more successful business. But, can innovation actually be a productivity killer? Today we look at how innovating may not always be the best way to get your business to go where you want it to go.
For businesses that get a lot of work done while out of the safety and privacy of their offices, the importance of having a secure way to connect employees to important assets and data cannot be understated. To achieve these ends, many organizations implement what’s called a Virtual Private Network, or VPN. But what is a VPN, and how does it work to protect your business while out of the office?
Project management can be an exceptionally tricky part of implementing any new solution or service for your business. While technology can help with this process, you’ll want to understand how its implementation helps in the grand scheme of things. We’ll help explain how value-based managed IT services can help you ensure projects are completed with minimal downtime and technology hiccups.
Ransomware has been a major problem for several years now, and 2018 continues to see this threat develop in unforeseen ways. Ransomware is malicious software that can encrypt data located on your device or network, with the encryption key only being available to those who pay a ransom. Ransomware is known today as one of the most pervasive threats out there. We’ll take a look at how ransomware has changed, what the future looks like, and how you can keep yourself safe.
It is interesting to see how different businesses deal with legacy computing systems. On one hand, these systems have been critical in getting your company to where they are today. On the other, they are getting old, and newer technology will almost assuredly improve aspects of your business, including security, software functionality, and computing efficiency. For this reason, companies that have a dedicated strategy in place to routinely upgrade their core technologies tend to run into fewer technology-related problems.